Secure Environment
Large installations are operated by many people, including system administrators, engineers and operators, business analysts mining data, company executives browsing reports, etc.
AggreGate offers a flexible and customizable security architecture for such complex multi-tenant environments.
Audit Trails
The AggreGate server keeps and reports all important events and activities, including security events. There are two security event processing channels:
- Internal events that can be persistently stored in a server database or routed according to the custom rules
- Logging engine that uses a file-based logging by default
Database Security
The platform server fully manages its own data storage. No system usage scenarios assume that it might be necessary to directly access any data stored in a server database.
Since all access to the database goes through the AggreGate Server core, all access attempts are authorized according to the internal role-based access control.
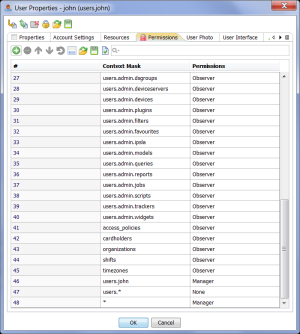
Role-Based Access Control
AggreGate internal user accounts have personal or shared permission tables that restrict access to the system resources and their groups, both local and remote.
Every attempt to access the server’s unified data model is validated according to the permissions of an authorized user.
Active system objects (such as alerts or models) inherit permissions of their owners once they access the unified model.
Communications Security
AggreGate communication protocol is used for data exchange between the primary platform components: servers, clients, and agents. This protocol supports the SSL/TLS encryption that is enabled by default.
All connections to the AggreGate Server through a unified console, browser interface or any API (such as SOAP or REST API) are always authenticated and authorized.
Security of data exchange between the AggreGate server and devices depends on the security and encryption options offered by the device's communication protocol. In the majority of cases, if a certain communication protocol supports some security and data encryption options, these options are also supported by a corresponding device driver. This enables secure device communications whenever possible.
If a certain amount of corporate services provided by AggreGate are publicly available, the servers installed in DMZ can get connected to the primary LAN-based servers via the TLS-secured distributed architecture links and have limited read-only access to the publicly available data.